Differential value
The International Electrotechnical Commission, (IEC) is developing a new family of standards. The 62443 standard, based on ISA99 work, specifies the security requirements for addressing external threats without losing any functional security features.
standard, based on ISA99 work, specifies the security requirements for addressing external threats without losing any functional security features.
One of the main security objectives of IEC 62443 is in-depth defense, taking into account low-level requirements, and extending security to other areas, from manufacturers to operators, in order to consider different attack surfaces.
It is meeting an enthusiastic reception from the industry, as it involves a methodology that is flexible, powerful and adaptable to different application objectives, keeping pace with the continuous evolution of technology, and starting from an exhaustive definition of requirements that together facilitate its implementation.
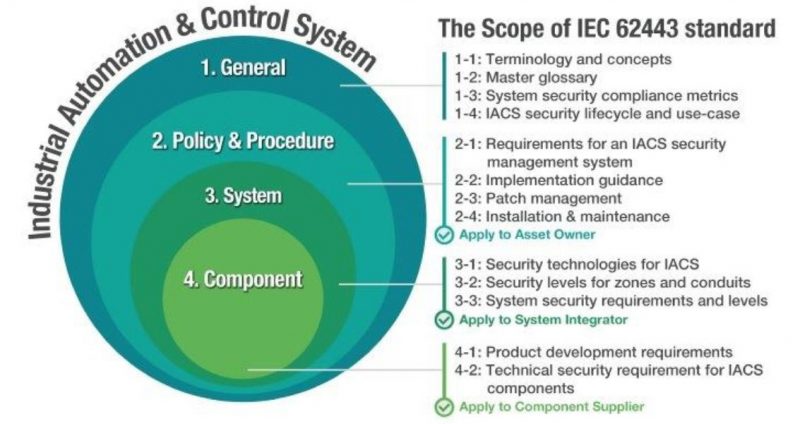
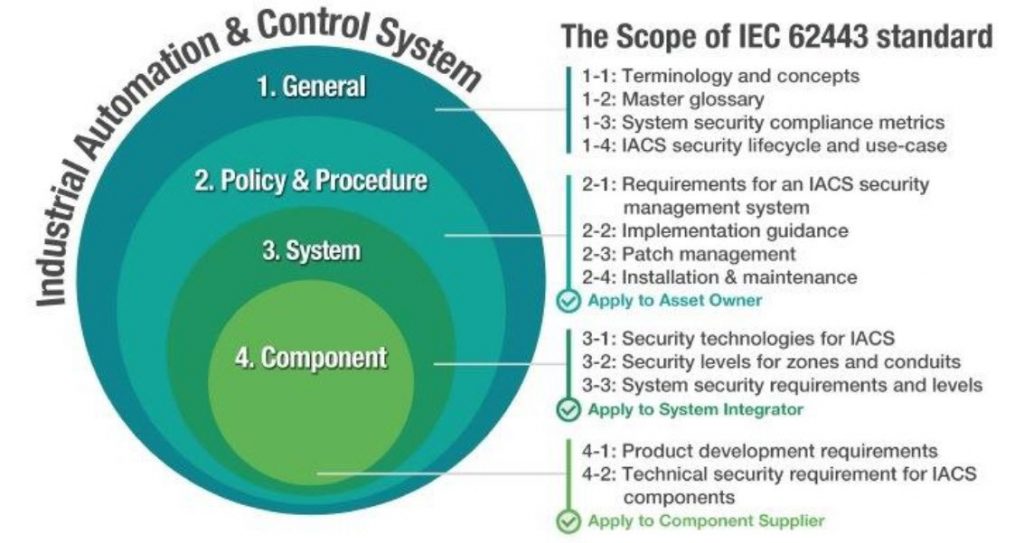 The figure shows the different parts that make up each standard, several of which are still in the development phase. However, it is expected that these will eventually be recognized as the de facto standard for cybersecurity, as IEC 61508 is for functional safety. The fact that it takes into account all these changes and brings together all the security measures will make IEC 62443 the most important cybersecurity standard.
The figure shows the different parts that make up each standard, several of which are still in the development phase. However, it is expected that these will eventually be recognized as the de facto standard for cybersecurity, as IEC 61508 is for functional safety. The fact that it takes into account all these changes and brings together all the security measures will make IEC 62443 the most important cybersecurity standard.
The scope of the application includes everything from the final IT system to the different subsystems and equipment involved, and even reaches the level of component parts, which is critical for its application to the new industry 4.0 and the related concept of IoT in the context of end consumers.
The assets to be protected are defined in a broad framework, suitable for each specific case and this is a far cry from the obsolete understanding of information theft. IEC 62443 establishes the assets and capacities to be protected as follows:
- Authorization
- Availability
- Confidentiality
- Acces
- Integrity
- Authentication
The two most important aspects or definitions of the measures found throughout the legislation are:
- Security zones: A group of physical or logical assets that share common security requirements. A zone clearly delimits the whole by defining a logical or physical border that separates internal and external parts.
- Gateways: These are communication paths between two security zones. They provide the security features that allow two zones to communicate securely. All communication between different areas has to be performed through a gateway.
This is important from a security perspective because, by grouping assets and allowing them to communicate via known routes, it is easier, in most cases, to put security measures in place that secure the conduits, rather than secure each asset independently.
The regulation describes a broad starting list of families of technical requirements, from Level 1 Foundational Requirements (FR) to specific Level 3 requirements, accompanied by active references to public libraries where the latest news and information is collected in order to facilitate the correct definition of cybersecurity requirements.
Alter Technology – IEC 62443 Methodology
In order to develop its cybersecurity services, Alter Technology TÜV NORD S.A.U. has created its own methodology for the analysis and application of IEC 62443, covering all necessary cybersecurity requirements applicable to industrial and end-user environments. Alter Technology offers end-to-end solutions that completely protect the attack surface, which is only possible with a deep knowledge of the needs of industrial services, along with a global vision, specialization, and innovation in cybersecurity.
The methodology addresses the analysis of the system or product under study, its vulnerabilities and assets, and the known threats and attack vectors, resulting in a final evaluation of the state of cybersecurity and the contingency plans to be implemented in order to obtain the target levels of cybersecurity.
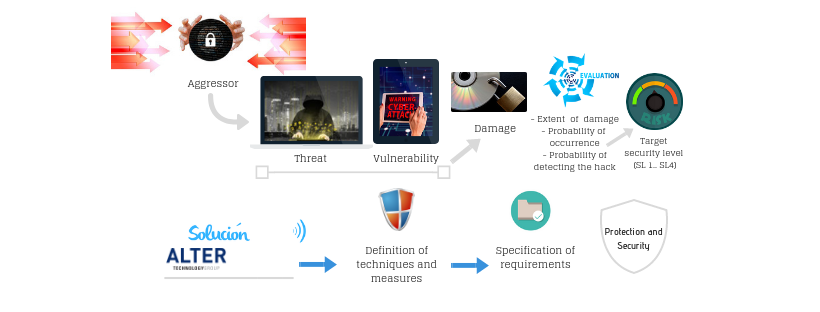
- The different stages of the methodology are as follows:
Understanding and breakdown of the system or product under study, its functionalities, and the most critical assets to protect. - Analysis of vulnerabilities.
- Segmentation of the system or product under study into security zones; identification of its access points and the interactions between zones; marking the assets to be protected.
- Study of external attack scenarios; identification of possible threats.
- Scenario cross-checking between the system or known product and external attack options. Assessment of the impact on security; initial conclusions on the cybersecurity of the system.
- Mitigation measures and attainment of SL levels (1-4).
- Quantum Key Distribution - 7th November 2022
- Conducted Immunity - 20th May 2019
- Electrical transients Test - 2nd May 2019